In the rapidly evolving landscape of cloud computing, understanding the nuances of data flow is crucial for optimizing network performance and security. Two key concepts that often cause confusion are ingress vs egress. This blog post will delve into the intricacies of ingress vs egress, shedding light on their significance in cloud environments and providing valuable insights for network administrators and IT professionals. We’ll explore how these concepts impact various aspects of network management, from security and traffic optimization to compliance, scalability, and troubleshooting.
What is Ingress?
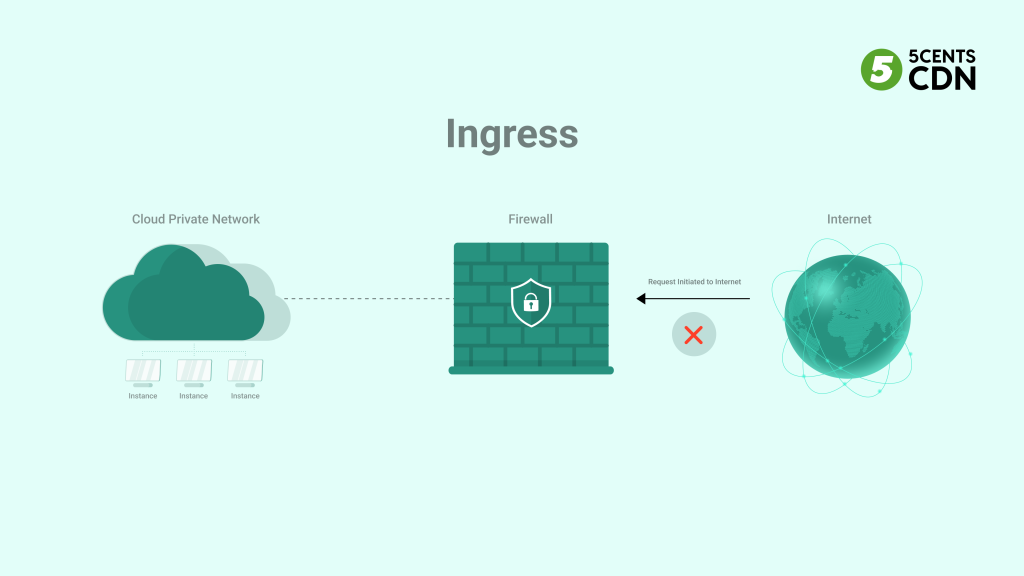
Ingress, in the context of cloud networking, refers to the flow of data into a network from an external source. This could be data coming from the internet, another network, or a user device, entering your cloud network. Think of it like the entry point to a secure building – all traffic must pass through ingress points, such as routers, firewalls, and load balancers, where it can be inspected and filtered. Proper management of ingress is essential for network security, as it allows you to control what data is allowed into your network and prevent malicious traffic from reaching your resources.
What is Egress?
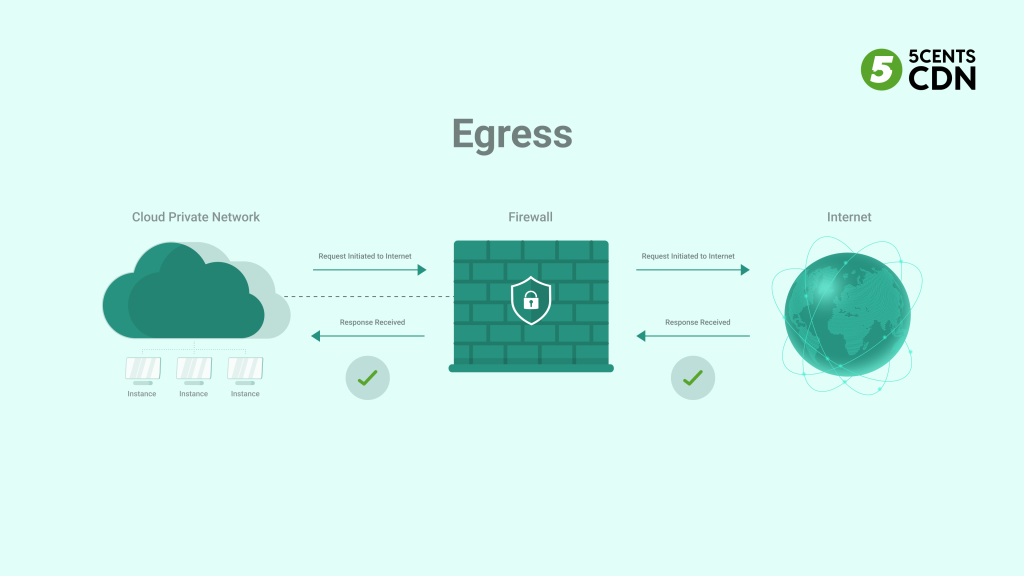
Egress, on the other hand, is the flow of data out of a network to an external destination. This could be data leaving your cloud network to reach the internet, another network, or a user device. Egress points are equally important for security and performance. They allow you to control which data is allowed to leave your network, preventing data exfiltration and ensuring compliance with data privacy regulations. Egress points can also be used to optimize outgoing traffic, prioritize critical applications, and manage bandwidth consumption.
Understanding Ingress vs Egress: Impact on Network Performance
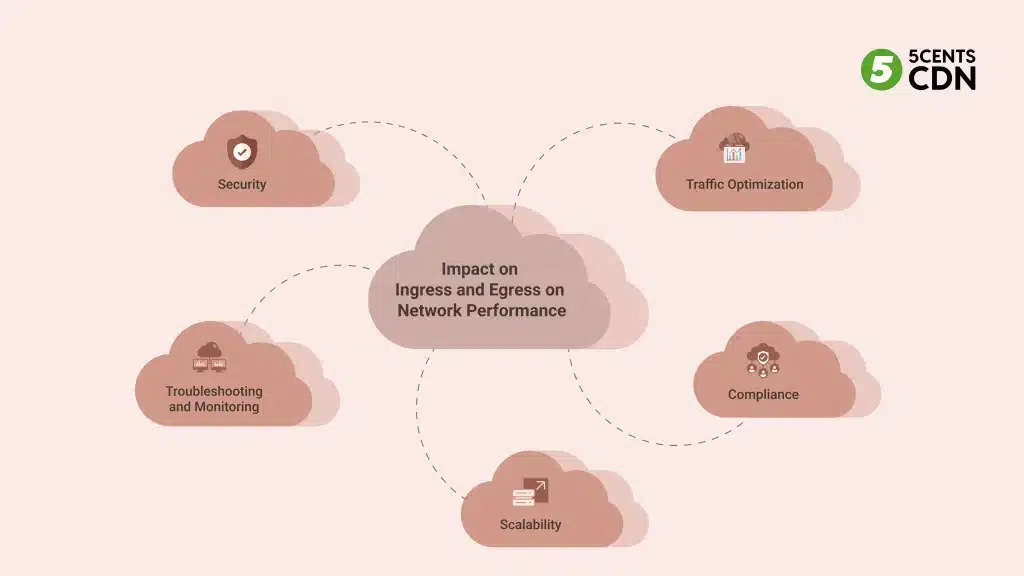
Efficient management of ingress vs egress points is paramount for optimal network performance. Here’s how these concepts influence different aspects of your cloud network:
1. Security Implications of Ingress vs Egress
Ingress points are the first line of defense against security threats. By implementing firewalls, intrusion detection systems, and other security measures at ingress points, you can filter malicious traffic, prevent unauthorized access, and protect your valuable data. Meanwhile, egress filtering helps prevent sensitive data from leaving your network without authorization, mitigating the risk of data breaches and ensuring compliance with data protection regulations.
2. Traffic Optimization
Egress points play a crucial role in optimizing network traffic. By implementing Quality of Service (QoS) policies at egress points, you can prioritize critical traffic, manage bandwidth consumption, and prevent congestion. This ensures that your applications have the necessary resources to perform optimally. Proper ingress management also contributes to traffic optimization by ensuring that only legitimate traffic enters your network, reducing the load on your infrastructure.
3. Compliance
Properly configured ingress and egress points are essential for meeting regulatory compliance requirements, such as GDPR, HIPAA, and PCI DSS. By controlling data flow and implementing appropriate security measures, you can ensure that your network adheres to industry standards and regulations.
4. Scalability
Efficient ingress and egress point management are fundamental for network scalability. As networks expand, scalable ingress and egress points accommodate increased data traffic, sustaining smooth data flow without compromising performance.
5. Troubleshooting and Monitoring
Ingress and egress points serve as critical monitoring and troubleshooting junctures. Through continuous monitoring and analysis of data traffic, administrators can detect anomalies, troubleshoot effectively, and ensure optimal network performance.
Best Practices for Ingress and Egress Management
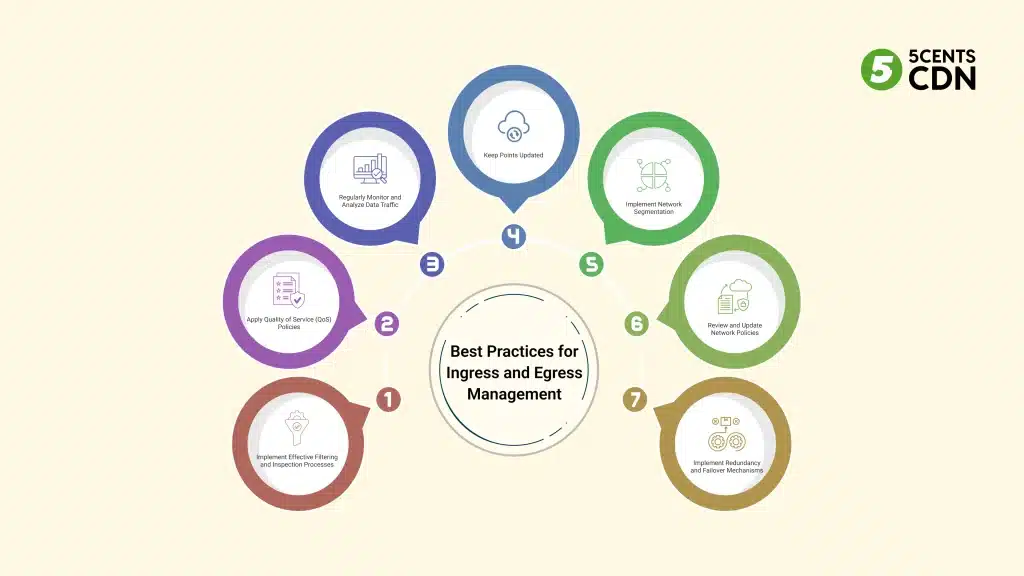
To effectively manage ingress vs egress in your cloud network, consider these best practices:
1. Implement Effective Filtering and Inspection Processes:
Safeguard networks by preventing unauthorized access through robust filtering and inspection processes at ingress points.
2. Apply Quality of Service (QoS) Policies:
Prioritize critical data traffic, manage congestion, and optimize data transmission by implementing QoS policies at egress points.
3. Regularly Monitor and Analyze Data Traffic:
Ensure optimal network performance by monitoring and analyzing data traffic at both ingress and egress points, facilitating proactive issue detection and resolution.
4. Keep Points Updated:
Regularly update ingress and egress points with the latest software, patches, and security configurations to protect against vulnerabilities and maintain compliance.
5. Implement Network Segmentation:
Enhance security by implementing proper network segmentation to restrict data flow between different network segments, preventing unauthorized access.
7. Review and Update Network Policies:
Align with changing business requirements and security best practices by regularly reviewing and updating network policies, access controls, and routing configurations.
8. Implement Redundancy and Failover Mechanisms:
Ensure high availability and fault tolerance by implementing redundancy and failover mechanisms at both ingress and egress points.
Conclusion
Ingress vs egress are fundamental concepts in cloud networking that significantly impact performance, security, and compliance. By understanding these concepts and implementing best practices, you can optimize your cloud network for efficiency, scalability, and resilience. Remember that effective management of ingress vs egress is an ongoing process that requires continuous monitoring, analysis, and adaptation to the evolving needs of your cloud environment.